This is a follow-up to the hardware based SSH keys post, to document the reverse i.e. from hardware SSH keys to file-based SSH keys. File based SSH keys are weaker since they’re on your hard drive in the clear but they are also convenient.
Windows 10
- Disable automatic startup of
start wsl-ssh-pagent.batif you added that from the previous blog post.
Start -> type ‘startup’ -> Startup Apps -> scroll tostart wsl-ssh-pagent.bat-> Toggle off.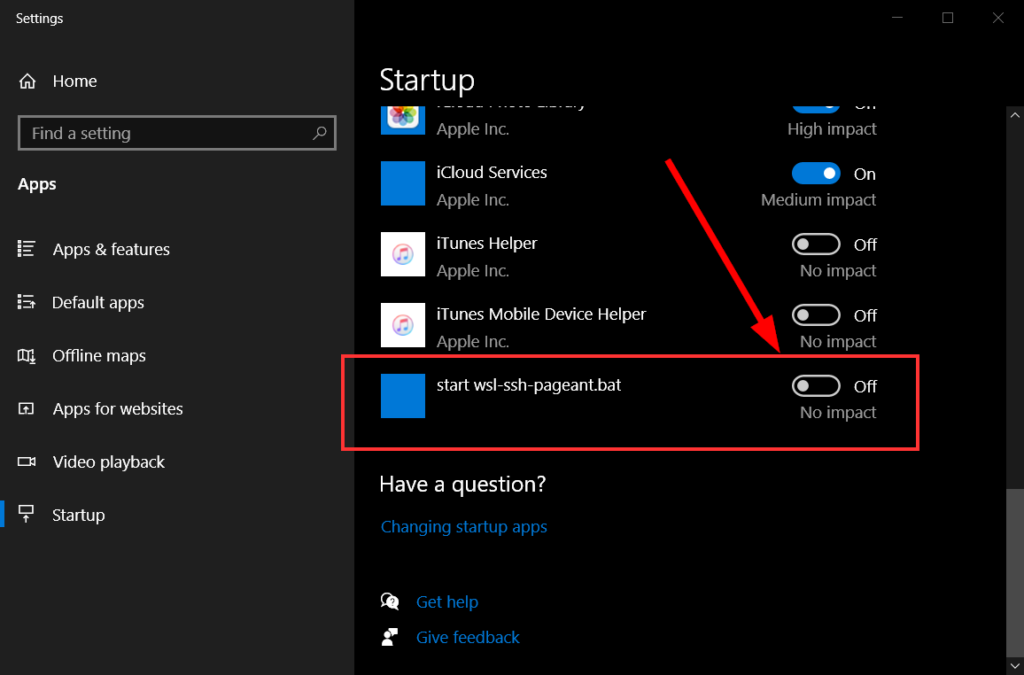
- You may need to update the OpenSSH binaries shipped in Windows 10 since even the Windows 10 v20.04 binaries can give an
agent returned different signature typeerror sometimes.- Download and unzip the file from https://github.com/PowerShell/Win32-OpenSSH/releases. I used the OpenSSH-Win64.zip file.
- Open an elevated PowerShell terminal by start -> type ‘powershell’ -> right click -> run as administrator
- Navigate to the folder where you extracted the files above and install by running the script
.\install-sshd.ps1
- Make sure you do NOT have the environment variable
SSH_AUTH_SOCKdefined. Type$env:SSH_AUTH_SOCKand hit enter in a powershell terminal. If it’s undefined, you should see no output, good! - Hit Start -> type “services” -> scroll to “OpenSSH Authentication Agent”. It should have status “Running” and Startup type “Automatic”.
WSL (Windows Subsystem for Linux)
- Open a WSL terminal
nano ~/.profile- add
{ eval ssh-agent; ssh-add /path/to/my/key; } &>/dev/nullat the end - comment or remove
export SSH_AUTH_SOCK=/mnt/c/tools/wsl-ssh-pageant/wsl-ssh-agent.sock(or similar) if you had previously added it